The food and beverage supply chain is under pressure. With 30% of food spoiling due to delays (USDA...
Securing 3PL PLC Networks: Mitigating Third-Party Cyber Risks
In the fast-paced world of third-party logistics (3PLs), Programmable Logic Controllers (PLCs) are the backbone of warehouse automation, managing everything from conveyor belts to inventory tracking. But there’s a hidden danger: many PLC networks are left open, granting third-party vendors unchecked access for support. While this access streamlines maintenance, it exposes 3PLs to devastating cyber attacks. As a fractional CTO who’s helped 3PLs like Nor-Cal secure their tech, I’ve seen how open PLC networks can become a gateway for hackers. In 2024, 35.5% of all breaches were third-party related, with 46.75% involving tech products (SecurityScorecard 2025). For 3PLs in industries like food and beverage, where downtime can spoil 30% of goods (USDA 2024), the stakes are even higher. This blog explores the risks of open PLC networks, key stats on third-party vulnerabilities, and actionable steps to lock down your systems.
The Hidden Risks of Open PLC Networks in 3PLs
PLCs are critical for 3PLs, automating processes like sorting and packing in warehouses. However, many 3PLs grant third-party vendors remote access to PLC networks for maintenance, often leaving these networks open and unsegmented. This creates a direct path for cyber attackers. If a vendor’s system is compromised, hackers can infiltrate the 3PL’s network, accessing sensitive data or halting operations. In 2023, 20% of data breaches were linked to third parties, with one telecommunications breach exposing 40 million customers’ data via vendor access (SecurityIntelligence 2024). For 3PLs, the impact is severe—downtime can cost $10,000 per hour, and spoilage of perishables can add millions in losses.
Open PLC networks are particularly vulnerable because they often lack basic security controls like encryption or access restrictions. A 2022 survey found only 13% of businesses formally review their suppliers’ cybersecurity risks (GOV.UK 2022). Worse, 62% of organizations don’t monitor third-party vendors’ security practices (Ponemon Institute 2023). This blind spot is a ticking time bomb. Hackers can exploit vendor access to deploy ransomware—41.4% of ransomware attacks in 2024 started through third parties (SecurityScorecard 2025). For food and beverage 3PLs, where speed is critical, a single breach can disrupt operations, spoil goods, and erode customer trust. Understanding these risks is the first step to securing your PLC network.
Key Stats: The Growing Threat of Third-Party Vendor Access
The cybersecurity landscape for 3PLs is increasingly perilous, especially with open PLC networks and third-party vendor access. Here are key stats that highlight the scale of the threat:
- Third-Party Breach Surge: In 2024, 35.5% of all breaches were third-party related, a significant rise from previous years, though underreporting suggests the true figure may be higher (SecurityScorecard 2025).
- Tech Sector Vulnerability: 46.75% of third-party breaches involved technology products and services, including PLC systems, as attackers target scalable entry points (SecurityScorecard 2025).
- Ransomware Connection: 41.4% of ransomware attacks now originate through third parties, with groups like CL0P exploiting vulnerabilities like the 2023 MOVEit zero-day attack (SecurityScorecard 2025).
- Industry Impact: Retail and hospitality, which often overlap with food and beverage 3PLs, saw the highest third-party breach rate at 52.4% in 2024 (SecurityScorecard 2025).
- Lack of Oversight: A 2023 survey revealed 62% of organizations do not monitor the cybersecurity practices of their third-party vendors, leaving PLC networks exposed (Ponemon Institute 2023).
- Financial Fallout: The average cost of a third-party cyber breach is 40% higher than an internal breach, often exceeding $10,000 per incident for PLC-related downtime (Gartner 2022).
These stats underscore the urgent need for 3PLs to secure their PLC networks. The graphic below illustrates the rising trend of third-party breaches, emphasizing why proactive measures are critical.
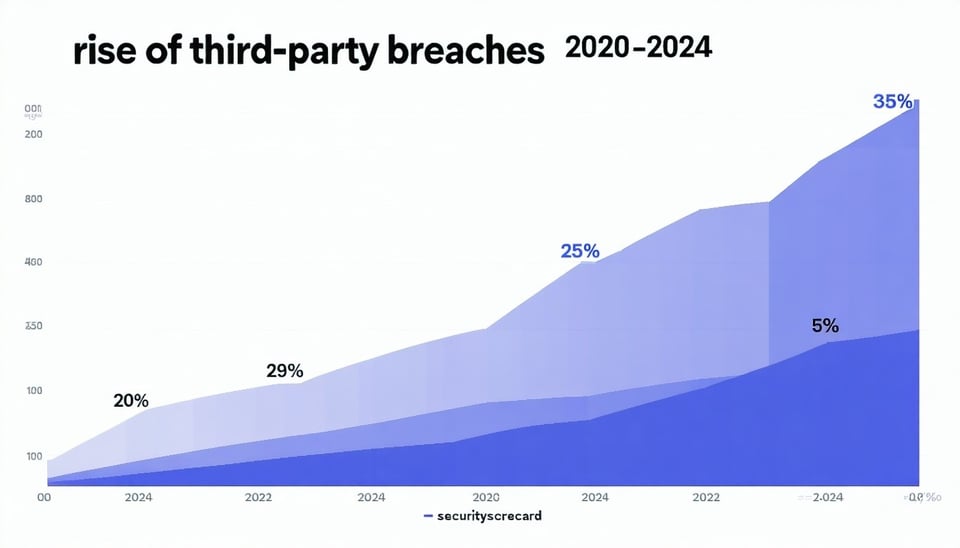
How Third-Party Vendor Access Amplifies PLC Vulnerabilities
Third-party vendors often require access to PLC networks for troubleshooting, updates, or monitoring. While this ensures operational continuity, it amplifies vulnerabilities when networks are left open. Many 3PLs fail to segment their PLC networks, meaning a vendor with access to one system can potentially reach the entire network. If a vendor’s system is breached, hackers can pivot to the 3PL’s infrastructure. In 2024, 64% of third-party breaches were linked to the CL0P ransomware gang, which exploited vulnerabilities like the MOVEit zero-day flaw (SecurityScorecard 2025).
Open PLC networks often lack basic security measures. For instance, 86% of surveyed organizations have never changed their router admin passwords, leaving devices open to default credential attacks (SecurityIntelligence 2024). PLCs, often connected to these networks, become easy targets. A compromised PLC can halt warehouse operations—imagine a beverage 3PL unable to sort orders during a holiday surge, leading to spoilage and lost revenue. Worse, attackers can steal sensitive data, like customer orders or employee records, as seen in the 2023 AT&T breach, where 9 million accounts were exposed via a vendor (FortifyData 2023).
The lack of visibility into vendor security practices compounds the issue. Only 31% of executives have a formal understanding of Nth-party risks, leaving 3PLs blind to vulnerabilities in their vendors’ ecosystems (PwC 2022). Without strict access controls, encryption, and monitoring, third-party vendor access to PLC networks becomes a cyber attack waiting to happen. 3PLs must act swiftly to close these gaps and protect their operations.
Steps to Secure PLC Networks and Mitigate Vendor Risks
Securing PLC networks in 3PLs requires a proactive approach to mitigate third-party vendor risks. Here are actionable steps to lock down your systems:
- Segment PLC Networks: Isolate PLC networks from the broader IT infrastructure using VLANs or air-gapping. This ensures that even if a vendor’s access is compromised, attackers can’t move laterally. For example, a food and beverage 3PL can separate its cold chain PLCs from corporate systems, limiting exposure.
- Restrict Vendor Access: Implement least-privilege access for third-party vendors. Use role-based access controls (RBAC) to ensure vendors only reach the PLC systems they need for support. In 2024, 54% of organizations lacked a comprehensive inventory of third-party access, a gap that must be closed (SecureLink 2021).
- Encrypt and Monitor Connections: Encrypt all remote access to PLC networks using VPNs or secure protocols like SSH. Deploy intrusion detection systems (IDS) to monitor for unusual activity. A 2023 breach at a telecommunications provider showed how unencrypted vendor access exposed 40 million customers’ data (SecurityIntelligence 2024).
- Vet Vendor Security Practices: Conduct thorough assessments of vendors’ cybersecurity posture before granting access. Review their security policies, incident history, and compliance with standards like SOC 2. Only 13% of businesses formally review supplier risks, a practice 3PLs must adopt (GOV.UK 2022).
- Implement Regular Audits and Training: Schedule quarterly audits of PLC network access logs and vendor activity. Train staff to recognize phishing attempts, which often target vendors—phishing attacks rose 4,151% since 2022 (SlashNext 2024). A well-trained team can prevent breaches that exploit human error.
- Prepare an Incident Response Plan: Develop a response plan for PLC network breaches, including isolating affected systems and notifying vendors. Tabletop exercises with vendors can test the plan’s effectiveness, as recommended by Marsh (2024).
By taking these steps, 3PLs can significantly reduce the risk of a cyber attack through open PLC networks, ensuring operational continuity and data security.
Conclusion
Open PLC networks are a cyber attack waiting to happen, especially with third-party vendors having unchecked access. With 35.5% of breaches in 2024 tied to third parties and 41.4% of ransomware attacks starting through vendors, the risks are undeniable (SecurityScorecard 2025). For food and beverage 3PLs, a single breach can lead to spoilage, downtime, and reputational damage. As a fractional CTO who’s secured 3PLs like Nor-Cal, I’ve seen how proper network segmentation, access controls, and vendor vetting can prevent disaster. Don’t let your PLC network be the weak link in your supply chain. Take action now—secure your systems, protect your operations, and safeguard your customers. Let’s lock down your network before hackers strike.



